Most Microsoft-based Hybrid Identity implementations use Active Directory Federation Services (AD FS) Servers, Web Application Proxies and Azure AD Connect installations. In this series, labeled Hardening Hybrid Identity, we're looking at hardening these implementations, using recommended practices.
You can control a virtual machine (VM) instance on Compute Engine like any standard Windows server. This tutorial shows you how to deploy a simple IIS web server so you can learn the basics of running a web server on a VM. Before you begin. You'll need a new Windows instance with HTTP traffic allowed. Diablo 2 runeword mod.
Note:
This blogpost assumes all Web Application Proxies, AD FS servers and Azure AD Connect installations run Windows Server 2016.
Hardening provides additional layers to defense in depth approaches. It changes the default behavior of products and services to make them more resilient to unauthorized changes and compromise.
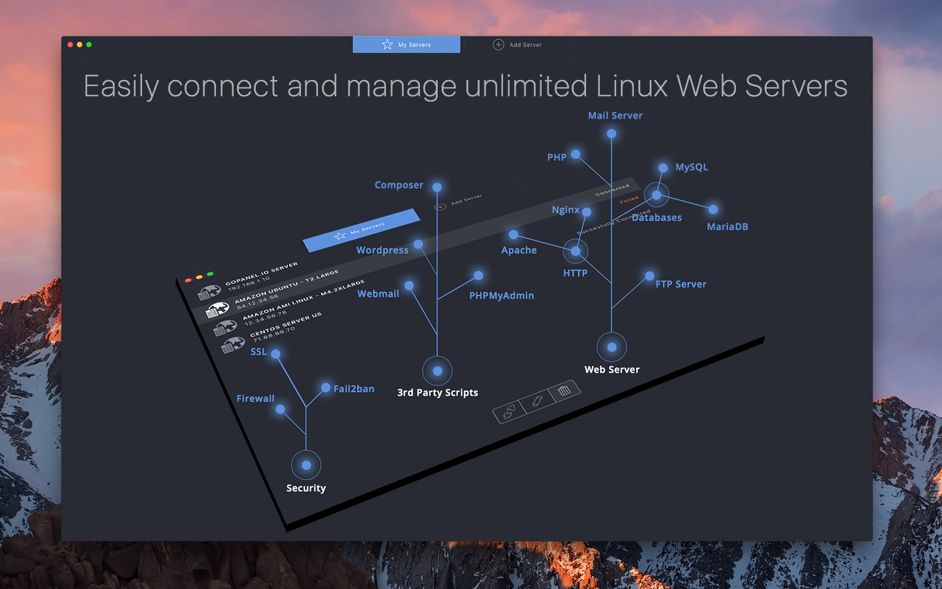
- GoPanel 2.7.0 is the most intuitive OSX App to manage web servers, an alternative to existing control panel softwares you install on your Unix based servers for web hosting. Easy to install and configure Apache, php, mysql, ftp, domains and emails on your server goPanel APP lets you easily connect and manage UNLIMITED linux servers.
- When the File Download window appears, click Save to save the file to your hard drive. NOTE - The file contains the compressed 64-bit Open Manage Server Administrator installer. Extract Files 1. Browse to the location where the file is downloaded and double-click the new file to unzip the downloaded package. Specify the location to unzip.
- Download file - goPanel22.5.0TNT.zip.
Reasons why
Protocols, cipher suites and hashing algorithms are used to encrypt communications in every Hybrid Identity implementation. Typically, ciphers and algorithms to use are based on a negotiation between both ends of a communications channel. The purpose is to use the most secure protocols, cipher suites and hashing algorithms that both ends support. To use the strongest ciphers and algorithms it's important to disable the ciphers and algorithms you no longer want to see used.
Microsoft recommends organizations to use strong protocols, cipher suites and hashing algorithms. For Azure Active Directory, they are changing the negotiation settings on their systems regularly, to avoid downgrades in encryption standards.
Possible negative impact (What could go wrong?)
When the systems of an Hybrid Identity implementation are improperly hardened, there will be no communication between Azure Active Directory and the systems of the implementation, and/or between the systems of the Hybrid Identity implementation.
This may affect authentications directly when using Active Directory Federation Services (AD FS) or Pass-through Authentication as authentication method in the Hybrid Identity implementation. This may cause diminished functionality, when Password Hash Sync (PHS) is used as the authentication method. Also, this may cause certificates to expire, monitoring to halt and/or backups to fail. It may also mean admins will no longer be able to (remotely) manage the systems.
When using the Remote Desktop Protocol (RDP) to manage the Windows Server installations of the Hybrid Identity implementation, the default security layer in RDP is set to Negotiate which supports both SSL (TLS 1.0) and the RDP Security Layer. Open Remote Desktop Session Host Configuration in Administrative Tools and double-click RDP-Tcp under the Connections group. If it is set to SSL (TLS 1.0) and you are running Windows Server 2008, make sure that you have installed TLS 1.1 and 1.2 support.
For Hybrid Identity implementations featuring Azure AD Connect's Seamless Single Sign-on (3SO), do not disable RC4_HMAC_MD5 at this time, as this may break.
To disable weak protocols, cipher suites and hashing algorithms on Web Application Proxies, AD FS Servers and Windows Servers running Azure AD Connect, make sure to meet the following requirements:
System requirements
Make sure all systems in scope are installed with the latest cumulative Windows Updates. Also make sure you run the latest stable version of Azure AD Connect.
Privilege requirements
Make sure to sign in with an account that has privileges to create and/or change and link Group Policy objects to the Organizational Unit (OU) in which the systems in scope reside.
Who to communicate to
When intending to make changes to systems in the Hybrid Identity implementation, make sure to send a heads-up to these people and/or teams in your organization:
- Load balancers and networking guys and gals
- The Active Directory team
- The people responsible for backups, restores and disaster recovery
- The people going through the logs, using a SIEM and/or a TSCM solution
- The monitoring team
One of the challenges you can easily avoid through communications is that multiple persons and/or teams make changes to the configuration. When it breaks, you don't want to roll-back a bunch of changes, just the one that broke it. Make sure you have the proper freeze/unfreeze moments to achieve that.
Encryption methods are comprised of:
- A protocol, like PCT, SSL and TLS
- A key exchange method, like ECDHE, DHE and RSA
- A cipher suite, like AES, MD5, RC4 and 3DES
Protocols
For the purpose of this blogpost, I'll stick to disabling the following protocols:
- PCT v1.0
- SSL v2
- SSL v3
- TLS v1.0
- TLS v1.1
Note:
PCT v1.0 is disabled by default on Windows Server Operating Systems.
SSL v2 is disabled, by default, in Windows Server 2016, and later versions of Windows Server.
Cipher suites and hashing algorithms
For the purpose of this blogpost, I'll stick to disabling the following ciphers suites and hashing algorithms:
- RC2
- RC4
- MD5
- 3DES
- DES
- NULL
- All cipher suites marked as EXPORT
Note:
NULL cipher suites provide no encryption. Scrutiny 8 1 10 – suite of web optimization tools.
Note:
The above list is a snapshot of weak ciphers and algorithms dating July 2019. Please consult the SSL Labs Documentation for actual guidance on weak ciphers and algorithms to disable for your organization.
For the purpose of this blogpost, I'll stick with the following protocols, cipher suites and hashing algorithms, in the following negotiation order:
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
This list provides a preference to Perfect Forwarding Secrecy (PFS) with the elliptic curve Diffie-Hellman key exchange (ECDHE_*) cipher suites.
As the systems in scope may or may not be of Active Directory Domain Services, may or may not run Server Core and may or may not allow downloading 3rd party tools, but in all cases you can disable weak protocols using Windows PowerShell with the following scripts:
Note:
As SSL v2 is disabled and removed from Windows Server 2016, and up, and SSL v3 is disabled by default in Windows Server 2016, and up, these protocols do not need to be disabled on Windows Server 2016, and newer versions of Windows Server.
Enable TLS 1.2
To enable TLS 1.2, run the following Windows PowerShell script in an elevated PowerShell window on each of the Windows Server installations in scope of the Hybrid Identity implementation:
Note:
The DisabledByDefault registry value doesn't mean that the protocol is disabled by default. It means the protocol isn't advertised as available by default during negotiations, but is available if specifically requested. Texpad 1 7 24 – latex editor.
Gopanel 2 1 0 – Manage Web Servers 1 8 Free
$SChannelRegPath='HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols'
New-Item$SChannelRegPath'TLS 1.2Server'-Force
New-Item$SChannelRegPath'TLS 1.2Client'-Force
New-ItemProperty -Path $SChannelRegPath'TLS 1.2Server' `
-NameEnabled-Value1-PropertyTypeDWORD
New-ItemProperty -Path $SChannelRegPath'TLS 1.2Server' `
-NameDisabledByDefault-Value0-PropertyTypeDWORD
New-ItemProperty -Path $SChannelRegPath'TLS 1.2Client' `
-NameEnabled-Value1-PropertyTypeDWORD
New-ItemProperty -Path $SChannelRegPath'TLS 1.2Client' `
-NameDisabledByDefault-Value0-PropertyTypeDWORD
Configuring .Net applications to use TLS 1.1 and TLS 1.2
Now, we need to configure .Net applications to use either TLS 1.1 or TLS 1.2. This is important for built-in Windows functionality and 3rd party applications and services. Run the following Windows PowerShell script in the same elevated PowerShell window as the previous one:
$RegPath1='HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319'
Gopanel 2 1 0 – Manage Web Servers 1 8 Bit
New-ItemProperty-path$RegPath1 `
-nameSystemDefaultTlsVersions-value1-PropertyTypeDWORD
New-ItemProperty -path $RegPath1 `
-nameSchUseStrongCrypto-value1-PropertyTypeDWORD
$RegPath2='HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319'
New-ItemProperty-path$RegPath2 `
-nameSystemDefaultTlsVersions-value1-PropertyTypeDWORD
New-ItemProperty -path $RegPath2 `
-nameSchUseStrongCrypto-value1-PropertyTypeDWORD
Disable TLS 1.0 and TLS 1.1
To disable TLS 1.0 and TLS 1.1, run the following Windows PowerShell script in the same elevated PowerShell window as the previous Windows PowerShell script on each of the Windows Server installations in scope of the Hybrid Identity implementation:
New-Item$SChannelRegPath-Name 'TLS 1.0'
New-Item$SChannelRegPath'TLS 1.0'-NameSERVER
New-ItemProperty -Path $SChannelRegPath'TLS 1.0SERVER'`
-NameEnabled-Value0-PropertyTypeDWORD
New-Item$SChannelRegPath'TLS 1.1Server' –force
New-Item$SChannelRegPath'TLS 1.1Client' –force
New-ItemProperty -Path $SChannelRegPath'TLS 1.1Server' `
-NameEnabled-Value 0 -PropertyTypeDWORD
New-ItemProperty -Path $SChannelRegPath'TLS 1.1Server' `
-NameDisabledByDefault-Value0-PropertyTypeDWORD
New-ItemProperty -Path $SChannelRegPath'TLS 1.1Client' `
-NameEnabled-Value 0 -PropertyTypeDWORD
New-ItemProperty -Path $SChannelRegPath'TLS 1.1Client' `
-NameDisabledByDefault-Value0-PropertyTypeDWORD
Restart each server after these configuration changes.
The systems in scope may or may not be of Active Directory Domain Services, may or may not run Server Core and may or may not allow downloading 3rd party tools. In all cases you can disable weak cipher suites and hashing algorithms by disabling individual TLS cipher suites using Windows PowerShell.
Note:
The below lines of PowerShell do not change the negotiation order of the cipher suites and hashing algorithms. It merely disables individual combinations of unwanted cipher suites and hashing algorithms. This also eliminates the need to keep up with the cipher suites in Windows Server between Windows Server version releases and even between updates.
A win-win situation if you'd ask me!
Tip!
To get an overview of the current negotiation order, use the following line of PowerShell:
Get-TlsCipherSuite|Format-TableName
Use the following lines on Windows Server 2016 installations to remove weak cipher suites and hashing algorithms:
Disable-TlsCipherSuite-Name'TLS_DHE_RSA_WITH_AES_256_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_DHE_RSA_WITH_AES_128_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_256_GCM_SHA384'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_128_GCM_SHA256'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_256_CBC_SHA256'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_128_CBC_SHA256'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_256_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_128_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_3DES_EDE_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_256_CBC_SHA256'
Disable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_128_CBC_SHA256'
Disable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_256_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_128_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_RC4_128_SHA'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_RC4_128_MD5'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_NULL_SHA256'
Disable-TlsCipherSuite-Name'TLS_RSA_WITH_NULL_SHA'
Disable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_256_GCM_SHA384'
Disable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_128_GCM_SHA256'
Disable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_256_CBC_SHA384'
Disable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_128_CBC_SHA256'
Disable-TlsCipherSuite-Name'TLS_PSK_WITH_NULL_SHA384'
Disable-TlsCipherSuite-Name'TLS_PSK_WITH_NULL_SHA256'
After hardening it's time to test the hardening. Everyone should sign off (not literally, unless that's procedure) on the correct working of the Windows Servers running Azure AD Connect. Does authentication to cloud applications still work? Does rolling over the certificate still work? Does monitoring still work? Can we still make back-ups? Can we still restore the backups we make?
Typically, hardening is rolled out to one Windows Server. When testing the hardening of the functionality behind the load balancer, make sure that the load balancer points you to the hardened system, not another one. In an environment with a Staging Mode Azure AD Connect installation, the hardening can be performed on this Windows Server installation and tested with the normal Staging Mode (imports only) synchronization cycles. When hardening is approved upon, the actively synchronizing Azure AD Connect installation can be switched, or hardened, too.
Note:
The registry changes are step 2 of two steps to harden protocols, cipher suites and hashing algorithms of the Hybrid Identity implementation. Make sure to Enforce Azure AD Connect to use TLS 1.2 only on the Windows Servers running Azure AD Connect, before testing.
Rolling Back Hardening
To roll back hardening, use the following lines of Windows PowerShell:
$SChannelRegPath='HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols'
1password 7 license. Remove-Item –Name'TLS 1.0' –Path$SChannelRegPath
Remove-Item –Name'TLS 1.1' –Path$SChannelRegPath
Remove-Item –Name'TLS 1.2' –Path$SChannelRegPath
Enable-TlsCipherSuite-Name'TLS_DHE_RSA_WITH_AES_256_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_DHE_RSA_WITH_AES_128_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_256_GCM_SHA384'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_128_GCM_SHA256'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_256_CBC_SHA256'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_128_CBC_SHA256'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_256_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_AES_128_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_3DES_EDE_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_256_CBC_SHA256'
Enable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_128_CBC_SHA256'
Enable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_256_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_AES_128_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_RC4_128_SHA'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_RC4_128_MD5'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_NULL_SHA256'
Enable-TlsCipherSuite-Name'TLS_RSA_WITH_NULL_SHA'
Enable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_256_GCM_SHA384'
Enable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_128_GCM_SHA256'
Enable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_256_CBC_SHA384'
Enable-TlsCipherSuite-Name'TLS_PSK_WITH_AES_128_CBC_SHA256'
Enable-TlsCipherSuite-Name'TLS_PSK_WITH_NULL_SHA384'
Enable-TlsCipherSuite-Name'TLS_PSK_WITH_NULL_SHA256'
Get rid of old protocols, cipher suites and hashing algorithms in your Hybrid Identity implementation, so they cannot be used to negotiate the security of the connections down.
Further reading
Managing SSL/TLS Protocols and Cipher Suites for AD FS
245030 How to restrict cryptographic algorithms and protocols in Schannel.dll
187498 How to disable PCT 1.0, SSL 2.0, SSL 3.0, or TLS 1.0 in IIS
Recommendations for TLS/SSL Cipher Hardening
How to Update Your Windows Server Cipher Suite for Better Security
A Cipher Best Practice: Configure IIS for SSL/TLS Protocol
Series Navigation
<< HOWTO: Enforce Azure AD Connect to use TLS 1.2 onlyHOWTO: Disable unnecessary AD FS endpoints >>-->easily connect and manage UNLIMITED linux servers
Intuitive
goPanel App provides an intuitive interface designed to simplify the process of managing web servers.
Flexible
goPanel is designed to function with either a dedicated server or a virtual private server. You can install and manage the following services: Apache or Nginx, PHP, MySQL or MariaDB, Mail Server and FTP.
Complete
Completely remote system so you don't have to install any software on your server. We provide the tools you need.
Safe
goPanel doesn't install any specialized software on your server and your credentials are stored safely on your mac.
everything you need to setup your linux server
Cutting Costs & Saving Time
goPanel lowers system administrator workload therefore saving you money. goPanel is the perfect solution to have your server setup and let you dedicate your energy to company growth.
User friendly
The app look and feel is taken as important as its feature set. The navigation feels like second nature along with visual appearance, interactive behavior and assistive capabilities.
Select Features
Everything you need to setup your server, web server, domains, emails, databases and ftp accounts. We're working continuously on many more features.
Reliable
We are a young team working to improve your experience, listen to your feedback along with your feature requests that should be included for next versions updates. We'll always have your back.
We provide you with the best features to make your job easier
One time payment and it's yours. No hidden costs or administrative charges.
- goPanel2 app
- One time payment, Unlimited servers, lifetime access.
$38.99$24.99- Web Server (Apache or Nginx, PHP, MySQL, FTP server, Mail)
- Security: Fail2Ban (intrusion prevention software)
- FREE SSL certs issued by Let's Encrypt certificate authority
- WP-CLI + One-click Wordpress installer
- PHPMyAdmin (database manager)
- Composer (application-level package manager)
- Cron jobs, backups and IP block manager
- Purchase goPanel
or download trial
What should you know before you make your purchase
The app only works on MAC OSX Systems - Yosemite or newer.
Please make sure you read our supported Linux distro and your server doesn't have apache or nginx, ftp, php, mysql, mail already installed as we do not support migration to existing services.
Read our FAQ and User Guide for more details https://downifile459.weebly.com/ishowu-instant-1-2-9.html.
Your purchase will offer you lifetime access to the app and also on multiple devices as iTunes terms (up to 10 Associated Devices, provided no more than 5 are iTunes-authorized computers.). We reserve the right to make some paid updates when we introduce new features. Please note that off App Store version of the app may be restricted to 1 or 2 uses per license depending on source of your purchase.
Unlimited servers, domains, emails only means that the app functionality is not limited or restricted in any way, you may still be limited by your server resources.
